Security 3 - Malware
Pre-Malware Category: Social Engineering Attacks
- Social engineering - talk to people, trick them into helping
- Famously, social engineering techniques are very effective
- e.g. call on the phone, claim to be an employee, ask for password info
- e.g. walk in campaign office, be the same age and look as the volunteers, ask what the password is to log in
- e.g. "Hi this is Larry, I'm on the client site to give a presentation, but it's a disaster. What's the password for the share drive again?"
- e.g. Walk in wearing overalls and with a clipboard, put a little black box on the printer. Really the black box is listening to all the local wi-fi packets trying to get a password
- Social engineering works because people are generally helpful
- Therefore: security is not just technology.
-Need to train people about social engineering too
-e.g. "Hi Larry, I'll call you back on your cell number on our list"
"Social engineering" means using human to human contact, say on the phone, to get into a system. Some people can be quite persuasive on the phone, and most people are polite and helpful by default (see, we're not such a bad species!). A bad guy might pose as technician showing up, trying to fix the printer. People will often be polite to a well dressed person on site who appears to be doing something proper. An example from a few years ago was leaving USB keys in the parking lot containing malware, counting on the curiosity of those picking them up and taking them inside and plug them in to their machines. Windows has (had?) an extremely insecure "autorun" feature where it will automatically run certain code on an inserted drive. On a properly designed operating system, plugging in a flash drive lets you look at its contents, not start trusting and running the bytes found there.
Malware Attacks
This is a big category, where the bad guy tricks the victim into running bad software ("malware") on the victim's computer. I'm lumping viruses, worms, and trojans all into this category.
How Do I Feel About This File?
- Suppose a bad guy emails you the following sort of file:
- .TXT file, which you open and read on your computer
- .JPG file, which you then open and look at on your computer
- .EXE program file -- a program or "app" to run on your computer
- .DOC document file which you then open and read on your computer
Passive Content = Safe, Program = Unsafe
- Program = unsafe
- If the bad guy authored code runs on our your computer..
the bad guy has won. It can do what they want
- The code can take actions and it's inside the computer
-watch all your keystrokes (keylogger)
-e.g. encrypt all your files
- "Malware" - generic term for program that does something bad
- Recall the "castle" analogy - the bad guy program is running inside the castle
- Variations below will all center on this downloaded ".EXE" case
- So we trust passive content (.TXT .JPG) but not active programs (.DOC .EXE).
- It's unfortunate that .DOC, can have "program" features, muddying security
-search for "doc macro virus"
The last, .exe case is the main risk here, although all of the above scenarios could result in problems. If code written by the bad guy, a .exe, runs on your computer, the bad guy now in essence has control and access to the data on your computer.
Suppose the bad guy is sitting at the keyboard of your unlocked computer, obviously they can do whatever they want with your data. The .exe case is very similar -- the code in the .exe could do what the bad guy wants -- look for a particular file, email it off the machine, etc. Most of the "attacks" listed below in essence try to re-create the .exe case, and the defenses center on preventing the .exe case.
"Malware" is the general term for a program written by the bad guy to do bad things to your machine - break in to the machine, steal passwords, send spam, etc.
Bad Guy Malware .EXE Techniques
Malware 1 - Trojan
- A "trojan" is malware disguised as something else
- So the user downloads it or accesses it, not aware that it will do something bad
- Program may be hidden inside a .zip archive of files
- e.g. JustinBieberJPEG.exe
- e.g. SuperAntiVirus.exe -- this is actually a common Trojan ruse!
- The trojan tries to look like harmless content, not a program
- Operating systems may have helpful warning "this is a program you downloaded, do you want to run it?" (below)
- Therefore: be very wary of running their program on your computer
- What I do: google the name/domain-name of it first, see what people say
- If something is from a well known domain and has lots of downloads, I figure someone would have flagged it if it were malware
Here is the Mac OS X warning that you are double clicking something that is a program to run...
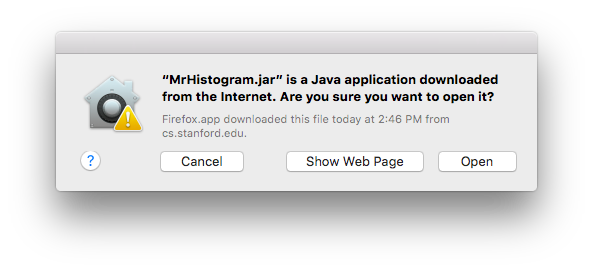
A "trojan" is a malware disguised as something else, like "awesome-cursors.exe" or "fun-game.exe" or "JustinBeiber.JPEG.exe" (Windows is vulnerable to extensions other than .exe, it's just used for the examples here). The term refers to the Trojan Horse story from antiquity. If the user can be tricked into double clicking the trojan, running it, then the bad guys have won. The https is no defense.
Malware Example - Keylogger
- A good example piece of malware - its running on your computer
- Keylogger - watches the screen, what urls you visit, records all the keystrokes
- HTTPS is no help - it's inside the castle
- Sends this info back to the bad guy
- Easy to imagine how this could allow the bad guy to abuse your accounts
- Important: do not log into your email account from some random internet-cafe machine!
Malware 2 - Vulnerability
- Vulnerability - an accidental hole in a program (a bug)
- e.g. a bug in the Flash animation program
- When fed an exploit of the vulnerability (a special pathological pattern of bytes) the program breaks and gives access to the machine
- So the bad guy writes this exploit file, and then sends links to it on sites or in spam
- Just visiting the page containing the exploit is enough to compromise the visiting machine if it is vulnerable
- Aka "watering hole attack"
-Bad guy places exploit bytes on web site, waits for victims to visit
- This is probably the most scary case, as the user does very little
- Solution:
- Keep web-facing software up to date
- All browsers now have strong auto-update channels, so by default the right thing tends to happen
- Keep disconnected backups of important files
Suppose there is an engineering flaw in Firefox or the Flash player or some other software on your machine, such that if it sees a particular sequence of bytes as input, there is bug that allows a takeover of the machine. This is called a "vulnerability", and it is one of the scary cases. If the user browses over to a web site this is hosting the "attack" content and their browser is vulnerable, then the bad guy can get it just from that. The bad guy can make the web site appear attractive, post links on reddit or whatever to try to drive traffic to the site. This attack is scary because it does not require the user to do anything especially foolish.
Such vulnerabilities in Flash and IE used to be quite common. However, the engineering culture seems to be catching up, and this case is becoming more rare. The most important step is being sure to run the most up to date, current version of your browser and any plugins such as Flash. Firefox et al have switched to make programs auto-check for new versions, so the user does not need to do much to have the most recent version. Often a vulnerability is fixed, and months later attackers start using it on sites, but they can still succeed with users using old versions.
Zero-Day Vulnerability
- The most scary case
- "Zero-day" vulnerability = no fix is available yet
- "Exploited in the wild" = bad guys are actively using this now
Web news search: zero-day vulnerability
- What does this headline mean "Adobe flash vulnerability found, exploits seen in the wild, update now."
- Translation: a new vulnerability bug has been discovered in Adobe's flash player. Exploits of this bug are seen out on the internet. The latest version of Flash fixes the bug, install it now. Increasingly, Flash and the browsers and whatnot detect new versions and install them automatically precisely because of this "vulnerability" scenario.
- "Zero-day" means a vulnerability in the wild before Adobe has a fix out
- Aside: this is also why having a proprietary format like Flash be a key part of the internet is not a good architecture. People are very dependent on Adobe to fix the software very quickly, and Adobe's record has been very uneven.
Malware Example: Zombie Botnets
- A group of machines with malware on them allowing "bot herder" to control them
- How to obtain the zombies?
- -Bot herder sends out million emails pointing to a site that attacks a Flash vulnerability, installing the malware onto vulnerable machines
- The bot herder sends out commands for all the zombies to do something
- Botnets can be rented, there's an active botnet market in the bad-guy community (suggested interesting B-School research direction)
In parallel with other harm, the malware may set up the compromised machine as a "zombie" or "bot". A zombie is a machine, one of thousands, which all together form a "botnet". The owner of the botnet can distribute tasks to be done by all the zombies, like this: "ok everyone, here is a list of 10 million email addresses, start sending spam email to them." Because the number of zombies is large, the botnet can accomplish things that require a lot of machines. Sending spam is a great example. Another great example is doing dictionary-password attacks on random websites, as shown previously.
Malware Example - Encryption "Ransomware"
- Malware encrypts with a random password all the files on the victim machine, deletes the originals
- The victim must send the bad guys money (bitcoin) to get the "unencrypt" password
- The bad guys typically do send the password when given the money
- The scheme depends on the bad guys having a reputation of reliability
- Have backups of your important files!
WanaCry Ransomware Example - last week!
- There was a vulnerability in windows file sharing
- It had been fixed a couple months ago, but many machines did not apply it
-Issue that Microsoft (reasonably) charges to go to the new version
-Easy (mistake?) for users to just stay with old version
-Free open source operating system bonus!
- Wanacry malware spread itself, encrypted files, demanded bitcoins
- Bad guys in this case seemed to be a bit incompetent, not doing the encryption optimally
Malware Example - DDOS Attack
- "Distributed Denial of Service" DDOS attack
- Attackers coordinates a large number of machines to send many requests to a site all at once
- Overwhelm the site's connection to the internet with so many packets, it becomes effectively unreachable
- When bad guys "take down" a web site in the news, typically this means a DDOS attack done with zombie machines
- Technical Fix many DDOS techniques depend on sending packets with a forged ("spoofed") From: IP address field. The router upstream of the attacking zombie could block such forged packets from leaving their network to help blunt DDOS attacks. Nobody is very motivated to do this currently. If I were dictator of the internet, I would require it to reduce this silly pollution. (This is a tragedy of the commons.)
- Demo: search for "ddos attack" news
The zombies can also be used to "attack" a web site, by all trying to access it at the same time. With some tends of thousands of machines all hitting a site at the same time, it is possible to in effect make the site unavailable to the internet. This is called a "denial of service" (DOS) attack. It's not breaking into the site or stealing passwords or money; instead it's making the proper function of something unavailable.
Obviously the botnet is not paying the owner of the machine. The botnet is stealing the use of the machine from its proper owner. If a machine seems sluggish in regular use, and the networking lights are blinking like mad all the time... the machine may be a zombie. Like a parasite in the real world, the zombie software wants the machine to still mostly work for its owner, otherwise they would be motivated to clean it.
One problem with zombies is that the owners may not be all that motivated to fix it. The millions of compromised Windows machines out there are putting out this pollution that causes problems for us all. If you think a machine is a zombie, you should erase it and fix it. The zombie may be doing who knows what with your passwords, your data, there's too many risks.
In what would make a most interesting Business School case study, there are active markets in botnets. The botnet owners basically rent out their botnets for spamming or whatever use a bad guys wants to pay for that day.
Interesting Attack Example - CEO Payment Email Scam
- Get email password of finance manager at company
-by guessing, phishing, keylogger
- Study past emails about making wire transfers
- Study when the CEO is traveling
- Send an email pretending to be from the CEO like this:
Hi Bob, Im' traveling, to grab this deal, I need you to wire $25,000 to 11243-4732626 ASAP
- May break into CEO's account to send, it or just make it look like from CEO
to attack swimming.com bad guys register swimning.com, send mail from it
- Not a bulk targeted attack, bad guy effort required
- Bad guys at times have placed voice calls, pretending to be people
- Works because email about wiring money is the common practice
- Solution: have some other channel to verify, e.g. call the CEO to verify
