Assignment 5: Cars and Key Fobs
Overview
Almost all cars currently come with a key fob, which allows you to open the doors, and start the car. When you buy a car, the convenience is the compelling feature. You can leave the key fob in your pocket, and never again worry about having a physical key. It sounds great.
The implicit assumption you make is that the key fob system is secure, and that some random person with $50 of hardware can't drive off with your car. You have no real way to tell whether the car company did a reasonable job with their system, so you have to trust them. Unfortunately, that trust is not always warranted. And it isn't until people try to hack these systems that the problems come out. Problems that less scrupulous people may have already been exploiting.
Your Car's Key Fob
There are lots of different key fob systems. We'll start by looking at the key fob for my 2006 Prius. Key fobs use something called a Remote Keyless System (RKS). In the U.S. these operate at 315 MHz, +/- 2.5 MHz. My Prius key turned out to be at 312.590 MHz.The keyfobs are all listed in the FCC database. Watching for new entries is one of the ways people can tell when new car models are coming out. These will appear long before the official announcement.
You can figure out what frequency your key fob transmits on using your SDR and use GQRX or SDR# to monitor the spectrum. When you push a button on the fob, you should see a brief jump in the spectrum. You may need to shift the frequency band up or down by a couple of MHz to find the signal, mine was almost 2.5 MHz low.
One word of caution. Don't get too carried away pushing the button! The RKS system uses a rolling pseudo-randomly generated code. Both the key fob and the car keep in sync, so that the car recognizes the next code. However, if the key fob gets too far ahead in the sequence (100s of button pushes) the car won't recognize it. That makes the key (and the car) considerably less useful!
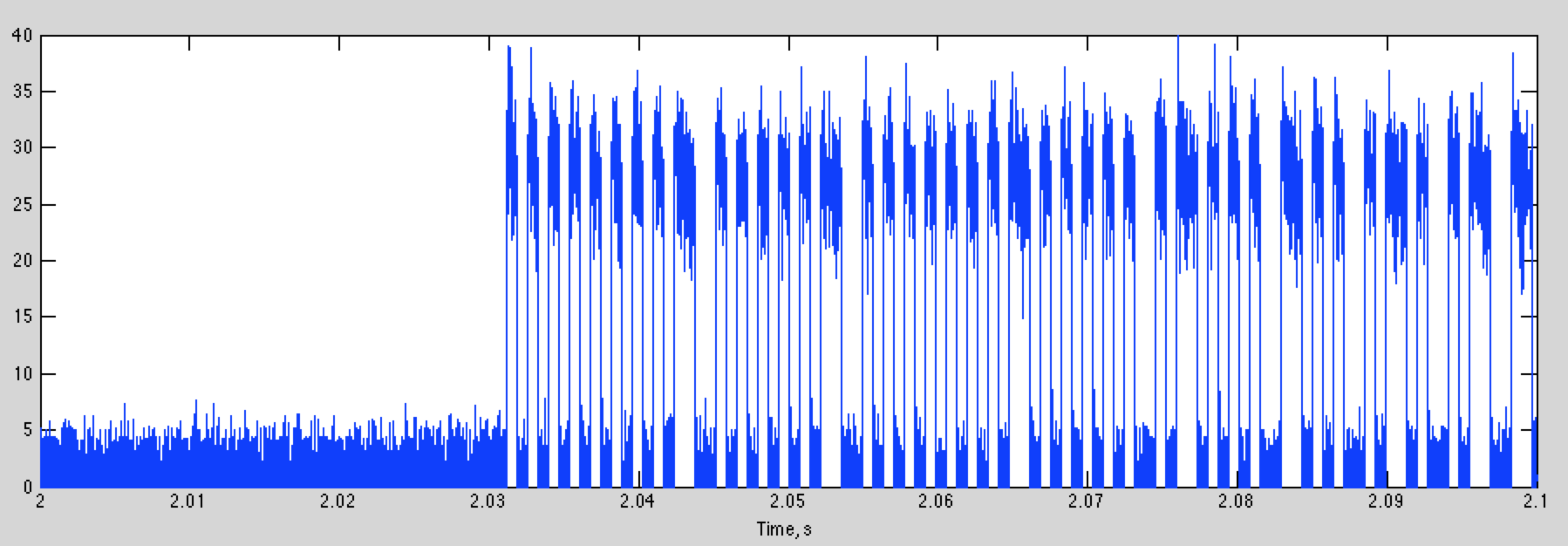
If we capture the signal the result is shown below

The total width of the plot is 10 seconds, so you can see there is one key press shortly after 2 seconds, and another shortly after 5 seconds.
If we plot 100 ms starting at 2 seconds, we can see the digital signal we are looking for:
Zooming in to the first couple of bits, we get

The bits are easy to identify. A decision threshold of 15 will give almost perfect detection. If we do this, and then plot first part of the digital data for the two key presses, we get this

Although the two start the same, they rapidly diverge. This is fortunate, because if the signal was the same every time, you'd have enough information to steal my car now!
The data is again on-off keying (OOK). It is also almost certainly split phase (or Manchester) encoding. Instead of a “1” being high, and a “0” being low, the information is encoding in the transition from high to low or low to high. That means that a “0” bit is a rising transition, and a “1” bit is a falling transition. A good way to recognize split phase encoding is that you can only have one or two low or high segments in a row. The nice thing about Manchester encoding is that every symbol has a transition, and these are easier to find then when the signal has been high or low for several intervals.
This example is OOK, which is the most common for car remotes. Some use frequency-shift keying (FSK), where each bit is transmitted as a different frequency, and the envelope is constant.
Attacks on Car Remotes
There are lots of different attacks that can be used against car remotes, depending on how they work, and what sort of access you are looking for. The simplest just let you open the car up. More thorough attacks give you complete control by basically cloning the remote.
Most key fobs use a rolling key. This produces a new waveform that depends on the ID of the key fob, a random seed, and how many times the key has been pressed. The car keeps track of the last code it received, and knows what the next several hundred codes might be. If it detects one of the expected future codes it opens the car. If it gets a previously used code, it stops responding to the key fob. For the Prius you have to do the “Chicken Dance” to get it to work again, provided you have another working key fob. Otherwise, you have to have the dealer rekey the car, for many hundreds of dollars. I have had to do this a couple times, now (for other reasons).
There are several lines of attack. One is simply recording the key fob output for a couple of button presses when it is away from the car, or the car is being jammed. With recorded unused codes, you can open the car.
Another is to reverse engineer the RKS sequence. In general this should be extremely hard. However, there have been several situations where this is very easy.
Finally, there are cars that open when the owner gets close to the car. This is based on a low power signal that can only be received when the key fob is very close. This can be defeated by amplifying these small signals.
There are many more attacks, and these will continue to multiply as cars get more complex, and have more embedded computer systems to go after. You can look at some of these for next week.
Replay Attacks
The oldest and simplest approach was to record the waveform that a key fob puts out (using your rtl-sdr), and then replay it. This works well for older garage door openers, that used a single fixed key. There are still cars out there that have key fobs that work this way (some pre-2000 Mercedes for example).
For key fobs that use a rolling key, you can still use a replay attack. If you can get access to the key fob when it is away from the car and record several key presses, you can replay these to have the car open.
If you can't get access to the key fob, a second approach is to make a device that records the output of the key fob when it is used, and simultaneously jams the car. A standard way to do this is to listen to the key fob transmission, and then start jamming when the error correction bits are transmitted at the end. That way you don't jam yourself. The car won't recognize the packet, but you can recreate the error correction bits, and retransmit the waveform later.
Finally, a jammer by itself will keep the remote from begin able to lock the car. If the driver isn't attentive, they may walk away from the car leaving it open.
Retransmission Devices
All of this depends on your ability to both transmit and receive RF. Your rtl-sdr's are just receivers, and do a great job of acquiring signals. There are lots of options for transmitting. There are a number of usb dongles that are based on the TI CC111X chips that are used in key fobs, like this one

An interesting, more flexible approach uses your Raspberry PI to generate RF by sending a carefully crafted data sequence to the GPIO port. This is described in detail, with videos, and links to the code here:
With this, you can generate pretty much any digital packet waveform you would like. Power levels are more than adequate for emulating a key fob. The rtl-sdr's are also well supported on the Raspberry PI, so the two together give you a total key fob hacking system for $50 or so, as we will see shortly.
Attacking Passive Keyless Entry and Start (PKES) Systems
Many higher end cars use a passive system for opening the car when the driver approaches. A low power signal is transmitted from the car as a challenge. The key fob then responds with an authentication. Because the power is so low, the car assumes the driver must be in close proximity if it receives a response.
These systems can be hacked by building a repeater that placed near the car. It captures the car's signal and retransmits it at higher power. The remote can be anywhere with in a couple hundred meters, and it will still hear the signal. The remote responds, and that is again captured by the repeater, and retransmitted. The car thinks the key fob is nearby and opens the car.

The nice thing about this approach is that you don't need to know anything about the key fob, except its frequency. You don't need to reverse engineer the protocol it uses, you are actually just using the real key!
Here is a video of some care thieves stealing a Tesla with this approach
Passive Remote Attack, Tesla Model 3
How can you reduce this risk?
Attacking the Rolling Key System
The next attacks go after the rolling key system itself. The way this generally works is that the key fob sends an ID, along with a counter of how many times a key has been pressed. This is encrypted, and transmitted to the car when you push the button.

If the encryption is strong, it is extremely difficult to figure out what the userid and counter is. There are several interesting cases. One is for the 20 years of VW's (and Audi's, Porsche's, etc), that we'll look at here. Another is for Subarus, that you can look at for your assignment this week.
A description of the VW RKS system is given here
This points to a Wired article (which unfortunately currently behind a paywall), and includes a technical paper that goes into great detail about how it works. The authors of the technical paper looked at the VW RKS systems for the last 20 years.
For the most recent systems, the encryption was relatively strong, equivalent to a 90 bit key. However, it turns out they used the same key in every car! 100 million of them!
The challenge then is to figure out what the key is, and what the encryption algorithm is. The car itself helps you solve that one. When button is pushed the car receives the signal, and then decodes it in the onboard computer (ECU). The key and the algorithm are stored in the ECU firmware. The authors bought some ECUs on EBay, downloaded the firmware, and reverse engineered the encryption (these are usually fairly simple bitwise operations that are easy to identify). With this knowledge, after acquiring the signal from a single key press, the user ID and counter can be decoded, and the key fob cloned, giving complete control of the car.
There are a couple of interesting things here. One is that every VW car decodes every key fob, so by monitoring the execution of your ECU, you can find the user ID and counter for all of the cars around you. There are reports of people using systems like this to steal other makes of cars, also.
The reason only your car responds to your remote is that your car has a “allow list” of key fob ID's it responds to. That is what gets set when you rekey the car.
This all sounds pretty alarming. But it gets worse, as we'll see next week.
Assignment
You have several options for your assignment this week. For each topic, generate about 5 slides to describe your thoughts or results. Sign up here
and upload your slides here:
1. This article concerns the Subaru RKS system. Read it, watch the videos, and describe what you find.
2. Have you ever wondered how those hotel key cards work? This article describes a non-RF hack that exploits the same ideas as the key fob attacks.
3. Why steal a car when you can have a bulldozer! Read this article, and watch the video, to see how this works.
4. There are lots of other car hacks out there. See if you can find something interesting, and describe it. Look for stories where you can figure out how it works. Entertainment systems are a common mode of access (check the Uconnect hack for Jeeps). Tesla and hackers have a long running cat-and-mouse game going. There are lots of interesting examples here. Two recent are Teslas and Hondas.
Finally, if you haven't already, please send me an email about how the class is going for you. I appreciate hearing your thoughts. Thanks!