Computer Security 1 - Attacks
Computer security is a big and kind of dramatic area, and it can look scary. I'll talk about the most important and interesting ideas. Keeping safe is not that hard.
Computer - The Castle
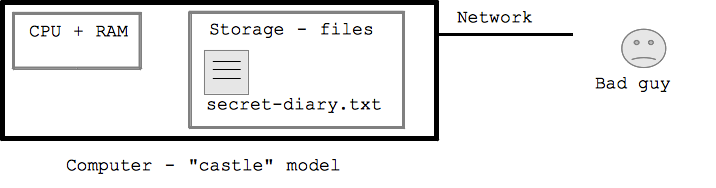
Computer Attacks
Below we'll tour through the three most common type of attack in broad categories, in particular looking first at ones you are most likely to experience: 1. Password attack, 2. Phishing attack, 3. Malware attack.
Special Category: Social Engineering Attacks
"Social engineering" means using human to human contact, say on the phone, to get into a system. Some people can be quite persuasive on the phone, and most people are polite and helpful by default (see, we're not such a bad species!). A bad guy might pose as technician showing up, trying to fix the printer. People will often be polite to a well dressed person on site who appears to be doing something proper. An example from a few years ago was leaving USB keys in the parking lot containing malware, counting on the curiosity of those picking them up and taking them inside and plug them in to their machines. Windows has (had?) an extremely stupid "autorun" feature where it will automatically run certain code on an inserted drive. On a properly designed operating system, plugging in a flash drive lets you look at its contents, not start trusting and running the bytes found there.
Bad Guy Attacks - Crude and Bulk
Although I'll talk about problems most of the time, don't get all scared. I use the internet all day long, I don't have any anti-virus software installed, and I have not had any problems. It probably helps that I don't use any Microsoft software, which is a popular target.
Category-1: Password Attacks
Category-1a: External Password Guessing
The bad guy could try to just guess your password, attempting to log in again and again, hoping to get lucky. They might know the username and just guess the password, or more likely they are guessing both. There are 86400 seconds in a day, and suppose your bank permits 1 login attempt per second. The bad guy could just go through the list of 100000 common passwords ("password", "password123", "janexyz", ...) trying to get lucky. This works, since they only need to guess correctly for a few accounts, and they can do the attack in bulk.
Clearly, the bank or whatever should detect thousands of bad logins and slow down or freeze the account. This can cause problems for the legitimate user however, so it's a balance. One simple policy is that the Bank can process login attempts at a slowish rate, such one every second to prevent the bad guys from trying 100 billion different passwords.
Dictionary Attack Example
Here's a real "log file" from my codingbat.com server where it routinely records what happens each day. What you see here is the attacker is trying guess both the username and password on the account. It happens that the username for each attempt is printed in the log file but the password is not. No doubt they are trying common passwords, such as "secret" "password12" etc. It's funny to me that you can see that their list of usernames to try is sort of alphabetical order, and they are just running through it in the most obvious way. So what you need to understand is .. this sort of attack is clicking along, every second of every day aimed at basically all the servers on the internet. They just need to succeed with a few accounts here and there, even though they fail 99.99% of the time. This is why you should not have a password which is close to a dictionary word or someone's name, or is a password people often choose. The good news is .. with just 4 random letters added to your password .. suddenly this dictionary attack is not going to work -- there's not enough seconds in the day. Note that 49.212.7.205 is the IP address of the machine attacking codingbat.com. It appears to be in Japan -- it's probably some person's Windows XP machine that has been compromised and is now used as a "zombie" under the control of the bad guy to launch more attacks. The zombie is probably running attacks at many servers all at the same time, but here we just see the ones directed at codingbat, about one login attempt every 3 seconds.
... Mar 6 06:26:20 codingbat sshd[30924]: Failed password for invalid user alex from 49.212.7.205 port 36268 ssh2 Mar 6 06:26:22 codingbat sshd[30926]: Failed password for invalid user alex from 49.212.7.205 port 36605 ssh2 Mar 6 06:26:26 codingbat sshd[30928]: Failed password for invalid user alex from 49.212.7.205 port 36937 ssh2 Mar 6 06:26:29 codingbat sshd[30930]: Failed password for invalid user adam from 49.212.7.205 port 37212 ssh2 Mar 6 06:26:32 codingbat sshd[30932]: Failed password for invalid user fax from 49.212.7.205 port 37546 ssh2 Mar 6 06:26:34 codingbat sshd[30934]: Failed password for invalid user fax from 49.212.7.205 port 37864 ssh2 Mar 6 06:26:38 codingbat sshd[30936]: Failed password for invalid user demo from 49.212.7.205 port 38201 ssh2 Mar 6 06:26:41 codingbat sshd[30938]: Failed password for invalid user demo from 49.212.7.205 port 38561 ssh2 Mar 6 06:26:44 codingbat sshd[30940]: Failed password for invalid user amanda from 49.212.7.205 port 38911 ssh2 Mar 6 06:26:47 codingbat sshd[30942]: Failed password for invalid user angie from 49.212.7.205 port 39244 ssh2 Mar 6 06:26:51 codingbat sshd[30944]: Failed password for invalid user angie from 49.212.7.205 port 39552 ssh2 ...
Bad Passwords
Good Passwords
You do not need a super elaborate password, but you don't want it to be susceptible to a dictionary attack either. My suggestions:
- The list of common passwords contains passwords that are just a word or a word plus a tiny variation, like "jane" or "secret1" or "mittens123", or two words like "catmittens", so it's vital that your password does not look like that.
- It's ok to have a word fragment, but it should also include significant nonsense letters. Personally, I like starting with a word, since it is easy to remember and fast to type, but then random junk needs to be added in and around it.
- Some sites go crazy, requiring many upper case letters, and digits, and punctuation letters. I think that's not necessary. It's "security theater": adding more complexity and the appearance of action but without actually adding to security.
For an important site like a bank, you should use a password different from your other passwords. It should not be the case that by stealing your facebook or twitter password, they now have access to your bank. I write the passwords down on a piece of paper at my house in case I forget. The bad guy in Russia or whatever does not have some team of ninjas that's going to break into my house and get passwords off my slip of paper. The attacks are bulk, mindless affairs that work on the low-hanging fruit. One technique for writing down passwords is to pick a little suffix you memorize, like "x936" or whatever, and that always goes on the end of all your passwords. Write the passwords down, but never the suffix. That way, even with the piece of paper, a bad guy still does not have the passwords. Or maybe its better to just write the passwords out clearly, so your family can access your email etc. if you are in the hospital.
Email is tricky -- once they have your email password, then they may be able to do a password reset and get into your account. In that sense, your email password is the most important.
Category 1b: Site Hacked - Encrypted Password Stolen, Cracked
Technical Fix - 2-Factor Authentication
Category-2: Phishing Attacks
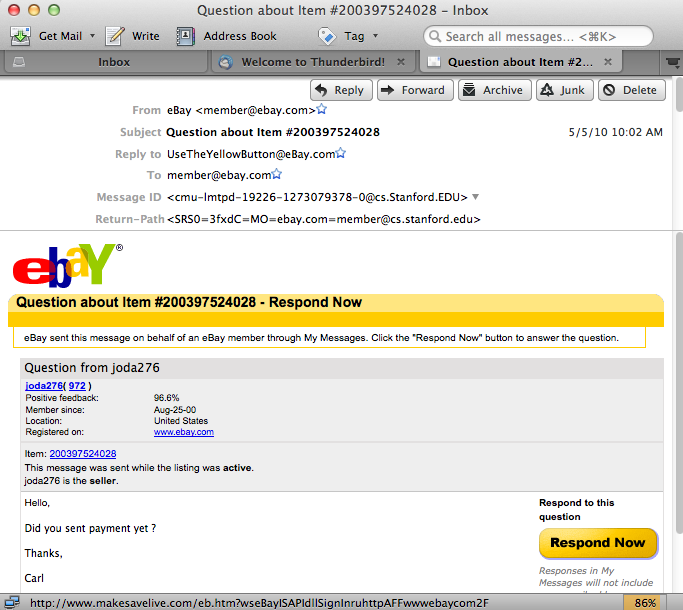
Probably the most common form of attack. The email is forged to appear from someone you might trust -- including logos etc -- I have gotten ones which I personally found quite convincing. I had to slow down and really pay attention to realize that it was a phishing attempt. It does not help that ATT, Schwab, Citigroup, etc. do in fact send you email all the time about your accounts.
Here is an example ebay phishing email sent to me. The arrow (not shown) is over the first blue link, so its url appears at the bottom of the message. Note that the url is not an ebay url, it's some bad guy url which will attempt to fool us into typing in our username/password. Note that there is no actual sale or anything that prompted this message -- the bad guys just spew out millions of these emails, in the hopes that one make sense to someone.
The most obvious valuable information the bad guy can get from you is a password to a bank account or some other account that contains something valuable. However as a simplification, if the bad guy can get the password to your email address, then they may be able to get access to most things by clicking the "I forgot my password" button on your bank site. So your email password is very important.
Fake ATM Machine -- Real World Analogy
Criminals put up a fake ATM machine made of plywood in front of a real ATM, with a "under construction" sign. The victim would put their card into the fake ATM and type in their PIN. Then the machine would print an "out of order" message and give the card back. The bad guys in this way collected all the card numbers and PINs and drained the accounts over the weekend. This is a nice real-world analog of fake-site phishing.
Avoiding Phishing
HTTPS
HTTPS is the "secure" http variant, https://www.ebay.com/. In particular, the server must hold a certificate which is verified beforehand by an authority that the server really represents www.ebay.com or whatever. You have to pay money and file some paperwork to get an https certificate -- hard for a bad guy to do, although not impossible. The idea with https is that the user can see the identity of who they are talking to. In the browser interface, https is typically accompanied by a little lock icon, and some banks etc. mention to their users to look for the lock. Having users pay attention 100% of the time is not a perfect security solution, but it helps.
Encryption vs. Bad Guy Packet Eavesdropping
When you go on to wifi and visit a web page and type something in ... the packets for all that are just being broadcast in the room, so anyone nearby can observe the packets, listening in (recall the ethernet-packet-broadcast material from the networking section). For the most part, this is harmless. In some cases, say when you are typing in a credit card number, you want the communication to be encrypted (encoded), so that someone listening in cannot read it. The https scheme above also does encryption, so you will notice that when you go the page to type in a credit card number, the url begins with "https://". On such page, all the packets are encrypted, so someone can listen and see the packets, but they will appear to be random garbage. The eavesdropper cannot unscramble the packets to see what's inside, or forge a packet. So Https blends two security provisions -- (a) verifying that it really is the www.mybank.com or whatever server on the other end and (b) encrypting all the packets of the communication.
Category 3: Malware Attacks/Vulnerabilities
This is a big category, where the bad guy tricks the victim into running bad software ("malware") on the victims computer. I'm lumping viruses, worms, and trojans all into this category.
How Do I Feel About This File?
Passive Content = Safe, Program = Unsafe
The last, .exe case is the main risk here, although all of the above scenarios could result in problems. If code written by the bad guy, a .exe, runs on your computer, the bad guy now in essence has control and access to the data on your computer.
Suppose the bad guy is sitting at the keyboard of your unlocked computer, obviously they can do whatever they want with your data. The .exe case is very similar -- the code in the .exe could do what the bad guy wants -- look for a particular file, email it off the machine, etc. Most of the "attacks" listed below in essence try to re-create the .exe case, and the defenses center on preventing the .exe case.
"Malware" is the general term for a program written by the bad guy to do bad things to your machine - break in to the machine, steal passwords, send spam, etc.
Bad Guy Malware .EXE Techniques
Malware 1 - Trojan
A "trojan" is a malware disguised as something else, like "awesome-cursors.exe" or "fun-game.exe" or "JustinBeiber.JPEG.exe" (Windows is vulnerable to extensions other than .exe, it's just used for the examples here). The term refers to the Trojan Horse story from antiquity. If the user can be tricked into double clicking the trojan, running it, then the bad guys have won. The https is no defense. On Mac OS X, heuristics have been added where it puts up a dialog "This was just downloaded and it is a program; are you sure you want to run it?"
Malware 2 - Vulnerability / Watering Hole
Suppose there is an engineering flaw in Firefox or the Flash player or some other software on your machine, such that if it sees a particular sequence of bytes as input, there is bug that allows a takeover of the machine. This is called a "vulnerability", and it is one of the scary cases. If the user browses over to a web site this is hosting the "attack" content and their browser is vulnerable, then the bad guy can get it just from that. The bad guy can make the web site appear attractive, post links on reddit or whatever to try to drive traffic to the site. This attack is scary because it does not require the user to do anything especially foolish.
Such vulnerabilities in Flash and IE used to be quite common. However, the engineering culture seems to be catching up, and this case is becoming more rare. In the second half of 2012, there were a bunch of vulnerabilities in the Java browser plug in, resulting in some big break ins. They seem to have been fixed now in 2013 massive bad press (the browser plug in you can turn off, but still use Java on your computer). The most important step is being sure to run the most up to date, current version of your browser and any plugins such as Flash. Firefox, Java, et al have switched to make programs auto-check for new versions, so the user does not need to do much to have the most recent version. Often a vulnerability is fixed, and months later attackers start using it on sites, but they can still succeed with users using old versions.