Snapchat Groups: Group Communication for Social Networks with Weak Ties
Last month, popular social media platform Snapchat introduced a new group chat feature. The new feature allows users to create a 24-hour instance of a group to share content with, using all the existing capabilities of individual “chats”. This seems to be the first group communication platform agile enough for the dynamics of social networks, thanks to Snapchat’s signature self-deleting nature of media.
Intuitively, group communication within social networks depends on the creator of the group, who also tends to be most shared connection amongst group members. In other words, group chats tend to be small network of the creator’s personal connections, which we can assume to be strong ties. But for the remaining group members, their connections within the network can be a varied combination of strong and weak ties. With groups self-deleting within 24 hours, there is far less tension at play for example if a group member has no ties except for the creator or predominantly weak ties within the network. This Snapchat feature ultimately results in less cognitive overload regarding who someone is sending notifications to or who someone is receiving notifications from. This feature also eliminates the need to leave or delete a group in which someone is no longer interested or invested in. By accommodating both the strong and weak ties within social networks over time, one can anticipate a higher volume of media sharing within the platform.
Work Hard, Play Hard? A Network Perspective
“Work hard, play hard” a saying that many college students wish to live by – a reference to the balance between academic and social pursuits that we all want, but struggle to achieve. What if I told you that your academic success, was dependent upon your social success? Before, you start thinking to yourself “Is this anonymous studmuffin saying that the more friends you have, the better your grades will be?” Not quite. Let’s dive into a study of social networks through an academic context.
Janice McCabe, a professor of sociology at Dartmouth University says that “student friendships can be classified into three types of networks: tight-knitters, samplers and compartmentalizers.” Students can be classified into these three categories by the following definition.
Tight Knitters: Tight-knitters are students that have a large and dense group of friends with high connectivity. In the context of this class, we can think of a network of nodes where every node is connected by edges to a majority of nodes in that network. i.e a large cluster with many edges. Socially, these are students who have lots of friends, who similar to themselves, have a lot of the same friends.
Compartmentalizers: Compartmentalizers are students who have multiple friend groups (generally 2 to 4). These friend groups are separate from each other in the sense that none of the friend groups are friends with another friend group. These people generally have a group of friends to satisfy different needs: one group for fun, one group for studies, one group for physical activity etc.
Samplers: Samplers have more one-on-one friendships as opposed to group friendships. Socially, these people are more isolated, because their individual connections stem from a wide range of places. We can think of someone who has a single friend from the football team, a single friend in his/her math class, a single friend from his dorm etc.

Figure: Above is a small network of friendships in an academic setting. STE would be classified as a sampler, while the large network is made up of compartmentalizers and tight-knitters
In McCabe’s network studies of friends within an academic setting (a study performed between the social network of 67 students at Midwestern University), she found a distinct correlation between these three groups, and academic performance. Although more data on the study can be found in her book “Connecting in College: How Friendship Networks Matter for Academics and Social Success“, the main takeaway can be summarized as follows. For tight knitters, and compartmentalizers, their academic success is definitively influenced by their network of peers. Those students who were in a network of peers consisting of high performers, or in the case of compartmentalizers, had one group of friends of high academic performers, exhibited high academic performance themselves. However, these networks are a 2-way street. The tight-knitters and compartmentalizers who had a network of peers that were low performers, were more likely to exhibit low academic performance themselves. Now the samplers, those who were socially isolated, were not boosted nor hindered by their social connections. Their performance was driven by their own abilities, and their own abilities alone.
Although this study had a small sample size, and did not imply any sort of causation (i.e students may perform better when their friends are high performers, because high performers tend to become friends, as opposed to the argument that being friends with high performers, boosts academic performance), but there is a definite correlation. All in all, it won’t hurt to surround yourself with high performing, driven, and intelligent friends. We’re at Stanford, how hard can it be?
https://phys.org/news/2016-10-friendship-networks-college-impact-students.html
http://journals.sagepub.com/doi/full/10.1177/1536504216662237
6 Degrees of Separation from Kylie Jenner
The mobile app Houseparty, released in February of 2016, has over one million daily active users and has become the latest trend social media trend for Generation Z, with 60% of its user base under the age of 24. As mentioned in the TechCrunch article, the app spiked at #3 in the iOS app charts in May. The trend has taken over Stanford’s campus, where I continually hear phrases such as “Oh Jacob is in the house!” or “I always get notified that Olivia is in the house.” I was curious how this platform, at a time when its increasingly difficult to effectively rollout a social media app, was able to launch into success.
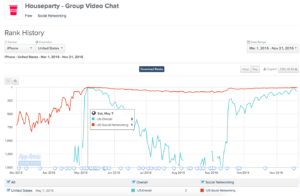
Houseparty is a livestreaming video app that enables users to split screens up to 8 times so that group of friends can laugh and chat together, taking away the “center of attention attitude of most social media apps now. As TechCrucnh explains, most other video streaming apps focus on just two individuals. As found Ben Rubin has described, the app is the “Internet’s living room.” As soon as you get online, you’re automatically “in the house,” meaning you can instantly video chat with any other friends also “in the house.” This means that users can video chat with any of their friends’ friends, including Kylie Jenner who has been rumored to use the social network frequently. The app changes the dynamics of social media networks. Instead of feeling the pressure of getting the most likes or comments or views on Snapchat, Facebook and Instagram, Houseparty takes the popularity contest out of social media. Users are no longer presenting a “filtered life” like they do on other apps. Houseparty allows for fluid conversations with friends, allowing the user to share the more authentic version of themselves with themselves.

The ease of quickly connecting and joining a “party” on the app, can allow the users to spend short burst of time goofing off with friends, relieving any stress. This is why I think may be why a flood of Stanford students have started using the app. Stanford students barely have any free time between their classes, clubs, sports, and other extracurricular activities. Houseparty allows students to congregate with friends in any short spans of time they have in their day—while walking to class, the 30 minutes you spend after dinner procrastinating. The app allows students to interact with friends who live all over campus, and catch up with multiple friends at once. Users can be in a livestream video with two of their friends and a friend of a friend could join, allowing users to expand their network. Because of the app’s unique ability to allow strangers to interact simply through a mutual friendship, the app exemplifies the proliferation of triadic closure – creating friendships across clusters.
Source: https://techcrunch.com/2016/11/21/the-internet-third-place/
Triadic Closure in the Animal Kingdom
Social networks and the theory of triadic are ideas generally applied to people, but recently a comprehensive study has mapped the social patterns of hyenas. Hyenas are advanced predators and live in large groups called clans. Within these clans, there exists a social network that develops similarly to those that we have discussed in lecture. The hyenas were very judicious when forming new relationships with members of their clans and predominantly chose to developed relationships with the friends of their friends, exhibiting triadic closure.
Triadic closure in the animal world makes sense as the hyenas that had existing relationships probably had similar traits and levels of fitness. The hyenas would logically choose to associate only with the other hyenas that would give them the best chance of survival, and determined that their friends were good judges of that ability. If hyenas exhibit this level of clustering, it is conceivable that other pack based hunters can utilize their networks to increase their chances of survival. Additionally, if they are forming triads, they probably also exhibit strong and weak ties that effect their propensity to mate, hunt, and interact.
Are you contributing to diversity?
You’re a senior, about to graduate from college, and the job search is on. You’ve done your homework, found companies you think will be a good fit for you and you, in turn, for them. But what is really going to make the difference? What will land you a job at one of your top picks? A referral.
If you have a friend, or a friend of a friend that knows someone at one of your prospective companies, your chances of getting a job there increase dramatically, a phenomenon known as the strength of weak ties (Granovetter). But this isn’t because as a referral you are inherently better than any other candidate; it is simply a byproduct of homophily.
Homophily: birds of a feather, flock together. The idea that you are friends with people like you – people with the same likes & dislikes, views on education & politics, and often, people of the same gender, ethnicity, & race. Take a look on social media or at the friends you hang out with at school. More likely than not, you will find this trend to be true.
So what does homophily imply for you as a referral? It means that you have been pegged as someone similar to your friend or friend of a friend. You are assumed to have the same values, priorities, passions, and work ethic as the employee who referred you. This is great! The company automatically trusts you more leading to a quick hire. You are thrilled because you landed a job, the employee who referred you is quite satisfied because they will most likely receive a monetary compensation for their referral, and finally, the company benefits because they saved money on their hiring process and you will likely remain at their company longer than if they hired a non-referral.
But we are forgetting something crucial. Not only do you have the same values as the employee who referred you, but you are likely of the same gender and race. The now indispensable weak tie that landed you your dream job also contributed to the lack of diversity that is plaguing many workplaces. According to a Bloomberg article, “Only 4 percent of Facebook’s U.S. employees are Hispanic and 2 percent are black, as of summer 2016—and those numbers haven’t moved in two years.” Similarly, Google’s staff continues to be approximately 70% male despite efforts to create a more diversified work place.
But why should companies care about fostering diversity? In addition to the social implications for gender and racial equality in the work place, diversity increases company performance. According to a McKinsey report from 2015, companies with gender, ethnic, and racial diversity can outperform companies of a less diversified background by up to 35%. This then begs the question, why haven’t efforts to increase diversity taken hold? Are the gains of diversifying worth the extra cost, effort, and time required to leave weak tie referrals behind?
So, as you continue forth in your search of what to do after graduation, be aware that those referrals from weak ties you hold so dear might be contributing to something that you morally do not endorse: a less diversified workplace. Just food for thought.
Source:
https://www.bloomberg.com/news/articles/2016-12-23/hiring-an-employee-s-buddy-is-fueling-a-major-workplace-crisis
https://sociology.stanford.edu/sites/default/files/publications/the_strength_of_weak_ties_and_exch_w-gans.pdf
What’s Next for Censorship?
Hold on to your brilliant new app inventions and future Snapchats, Stanford students, because you may be losing over 1.3 billion potential customers before your app even hits the market! It’s not news that China is heavy on the censorship, but a new measure by this global force – attempting to ban apps from the app store – is incredibly more effective and could become essentially “inescapable.”

In the new wave of censorship discussed in this NY Times article, the Chinese government has taken measures to limit the freedom of apps for mobile devices, in a few key ways. These include 1) having Apple remove the NY Times newspaper app from the Chinese App Store and 2) asking app stores all across the country to register with the government, supposedly to mitigate an “illegal information” spread, “user rights” violations, and for “security risks.” The Chinese government claims to take these measures to ensure transparency if any app store is found to engage in illegal practices, yet the consensus of this article is that it is only yet another measure to block the free spread of information across the world from Chinese residents. Russia has additionally pulled the app for the social network “LinkedIn” from the Apple App Store and Google Play Store for the country because the network refused to relocate information about Russian citizens to Russian servers. If this is just another case of censorship, then why could it be even more impactful?
Why is this change substantial? Well, controlling the world wide web versus apps are very different tactics, which poses the big problem in this article. Web information can be compared to a banned book, for example, which can be distributed in many ways (many different forms of transportation). If an app is banned, in contrast, it effectively doesn’t exist. It is the book that never even made it to the publisher, so the spread of information from that app cannot happen. The Chinese government is putting another chokehold on free speech.
The political tone of this article is complemented by that of a warning social tone. Chayka notes that growth of apps into a more central focus for consumers than the web was once a promise of decentralized communication, but warns against its power to become a mechanism of centralized control. Though partially deferent to the government, companies like Apple, Amazon, Google and Facebook have become the 4 main conglomerates of the internet’s central information platforms. Social, economic, and political considerations of these companies, such as profits from business with China, might perpetuate the censorship of information into the future.
What’s fascinating about the censorship issue, especially in light of the topics of this Networks class, is the potential changes of the social and political networks across the world. The internet and social media were designed to decentralize control, increasing the complexity of the social network as more and more apps and websites are developed. If China is blocking these apps, is the network going to break these edges, or will they attach to other nodes (like websites to circumvent firewalls, etc)? Is China going to become a gatekeeper for all information into the company? As for the 4 big tech companies, if we graphed social communication around the world, are they steadily becoming local gatekeepers or gatekeepers to most of our information? It’s interesting to consider the ramifications of China’s actions as well as the increasing power of Apple, Google, Facebook and Amazon on the graphing of social, economic, and political networks around the world.

ISIS: Twitter and Social Media Manipulator
The Islamic State in Iraq and Syria (ISIS) has captured news headlines for its global acts of extremism and terrorism. Unlike other terrorist groups, however, ISIS has been almost unprecedented in its large-scale exploitation of news and social media to garner influence, disseminate propaganda, and recruit supporters. Its effective use of social media applications such as Facebook, Twitter, Instagram, and Tumblr has enabled ISIS to expand the scope of its targeting efforts by capitalizing on “hyperactive users” who allow ISIS to draw on approximately 50,000 Twitter accounts.
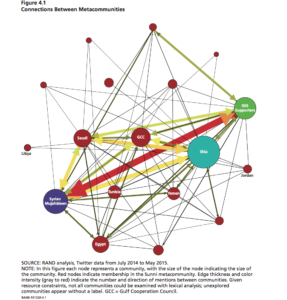
RAND corporation, a policy think tank located in Santa Monica, California, conducted a study on the impact of ISIS’ extremist messaging by analyzing social networks of communities that have been central to aiding ISIS, as well as those who have declaimed against ISIS, on Twitter. By querying Arabic-language tweets during the time period of July 2014 to April 2015, researchers were able to retrieve over 23 million tweets, which they then segmented into buckets in order to determine how to differentiate ISIS supporters and opponents on Twitter, the users’ messages, and how the various parties were connected.
I found the paper’s discussion on social network analysis in order to determine the strength and weakness of connections between communities involved in the ISIS Twitter conversation particularly fascinating and relevant to our class discussions and material. In RAND’s analysis, each node in the network represents “an entire community of user accounts,” while the edges between communities “aggregate the mentions between users in those respective communities.” By analyzing such relationships, researchers were able to paint a better picture of the geospatial layout of the communities, the influence of certain communities over others. For example, researchers found that the Syrian mujahideen community is vital to the network because of its position between ISIS supporters and more moderate communities. As such, it could “serve as an important influencer node to sway ISIS supporters with counter-messaging.”
The implications of the social network analysis of an extremist terrorist group are clear. In determining how various parties are connected in the network, intelligence analysts and researchers can perhaps make strides in identifying who and how to target ISIS supporters, aiding ISIS supporters, and potentially understanding power dynamics and key influential individuals in those communities by analyzing the number and extent of their connections to others through their Twitter account usage. Given my own interest and background in government intelligence, I found this paper highly intriguing due to its discussion on a topic at the intersection of how a seemingly colloquial area (social network and media, and, particularly, its underlying structure) can be used to better understand a group as relevant and serious to defense and national security as ISIS.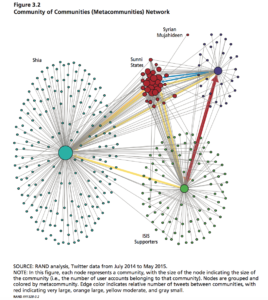
RAND Examining ISIS Support and Opposition Networks on Twitter:
http://www.rand.org/content/dam/rand/pubs/research_reports/RR1300/RR1328/RAND_RR1328.pdf
Breaking the Homogenized Network
In the midst of recruiting, college students are accustomed to handing out resumes listing their academic achievements or answering interview questions testing their cognitive capabilities. While students tend to focus on boosting their qualifications on these positions, there has been increasing emphasis on a somewhat divergent topic – networking – and with good reason. By expanding their social networks, individuals may just find that a single right connection can guarantee them a future career. Many companies, including tech giants like Palantir and Google, have depended heavily on referral programs to hire employees. A Bloomberg article argues, however, that the homophily present in referral networks may be detrimental to attempts to increase diversity in the workplace
Homophily encompasses the idea that “birds of a feather flock together,” or that individuals with similar traits tend to associate with each other. Studies indicate that race/ethnicity creates the most distinct separation in social networks; employees will refer friends who often have the same national origin or other demographic features as them. The result? The aggravation of between-group disparity and the loss of a potential performance boost associated with a diverse workforce. The referral program functions as a convenient tool for recruiting relatively successful hires, but the closed-loop network may very well be contributing to the lack of diversity in the workforce.
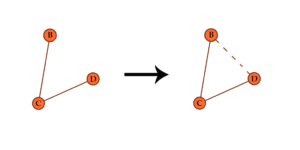
The high levels of success from referral hires make sense, when considering the ties between the different players. According to the triadic closure property, when two individuals share a mutual connection, there is a higher probability that they will form a link in the future. In this case, the employee has ties with both the company and the friend, increasing the chances that the company and the friend will develop a relation. The relationship, too, is likely to be positive given the transivity of trust passed on by the employee.
There are other reasons for the strong dependency on referral programs. As the article mentions, these social connections can help companies determine whether an individual is a good hire for a job. A referral hire will be inclined to share common characteristics with the employee; whether the mutual feature involves productive working habits, a sharp intellect, or an amicable temperament, the company will be prone to find positive qualities in the referred candidate similar to those that persuaded the company to hire the employee in the first place. Referral hires can be quite successful in developing a network of qualified employees; however, the dependence on these referrals may prevent perfectly competent candidates of different backgrounds from having an equal opportunity to join the workforce. Given these natural tendencies, the objective to create a diverse workplace may not simply involve companies accepting diverse candidates as they come but taking initiative to expand their networks beyond the current homogenized loop.
Modeling Innovation and the Emergence of Novelties
Innovation is, almost by definition, the way to change the game societies play, it happens all the time, and in all kinds of fields from technology, to language. Even though the idea of a revolution suggests a fortuitous event, it seems that a statistical look at the occurrence of breakthroughs shows remarkable regularities.
Just like with everything else, scientists tried to model innovation through math — in particular how new ideas or technologies arise, spread, and are adopted on a large scale. This endeavor seems to be especially significant considering that a lot of other models rely on expected values and predicting how the future will play out, thus without accurately accounting for innovation these predictions can become irrelevant. At the same time, the difficulty comes from what Zabell called “the unanticipated knowledge” — basically, any attempt at statistical inference runs into the problem that the space of possible outcomes (new ideas that could form) is unknown to us. This paper [https://arxiv.org/pdf/1701.00994v1.pdf] gives a great overview of advances on this topic.
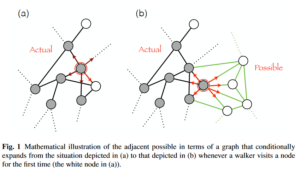
One notion that appeared in thinking about innovation patterns was that of the adjacent possible, referring to technology, words, molecules etc. that are reachable through combination and altering of existing knowledge. One way to think of this is that of a growing graph: whenever a node is visited (knowledge is created), this becomes part of the actual and all its neighbors are revealed, thus becoming part of the possible. The picture below is from the paper mentioned before.
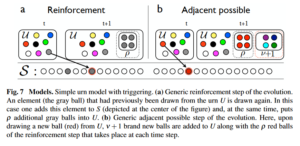
Empirical studies also give insight on innovation statistics. Heaps’ law concerns the law at which novelties happen, Zipf’s law gives the frequency distribution of the visited regions of the space, and we know signature correlations of how one novelty influences another. The authors of the paper, Vittorio Loreto et. al, created a new model that predicts these statistics. Their paper includes a review of the existing literature, which is worth reading in my opinion, although the computations could be skipped. The model proposed by Loreto is a combination of Polya’s urns and the adjacent possible. Polya’s urns account for evolutionary reinforcement: we extract a ball uniformly at random from an urn, and then put back two balls of the same color we extracted, thus increasing the chance we will select said color again. In Loreto’s model, a time series, the urn contains all pieces of knowledge (ideas, technology, words etc.); whenever we extract something that we haven’t seen before, our urn grows by adding a number of identical elements with the one extracted, but also a number of completely new elements adjacent to that one. They summarize the process in this image:
There is still much room for research on the topic, the difficulty coming from modeling the space of unknown, adjacent possibilities.
(just think that the space of adjacent possibilities would have to take into account people reaching what xkcd calls the Ballmer peak, https://xkcd.com/323/)
Friends
So it turns out that all of our friends actually have more friends than us. This pattern was discovered in 1991 while studying the nature of social networks. It is called the friendship paradox. This strange paradox occurs because of those people who are especially social. The idea is that only a few people have a large number of friends, but almost everyone knows one of those people that is especially social, and that has a large number of friends. So, once they’re friends with you, the average number of friends your friends have will go up. Therefore, your friends will have more friends than you on overage.
This idea was recently applied to see if it held up in social media. It turns out that it does. For instance, in the case of twitter, people were more likely to be following people with more followers, whether it be celebrities or just popular friends. This is definitely a very strange idea and I can see it even when looking at the network of my own friends. I follow people on social media that are celebrities or people with significantly more followers than me, and I have particular friends that are seen as much more popular.
http://metro.co.uk/2016/05/21/the-friendship-paradox-why-all-of-your-friends-have-more-friends-than-you-5896771/
Friend Request from the US government
People use social media sites for any number of different reasons – as a virtual photo album, a channel with which to talk to your high school sweetheart, or as home base for current event-related news. For some this information is carefully formulated before being posted on the web while others haphazardly throw up whatever information comes across their minds. You could go back and forth debating whether social media is an accurate representation of someone’s life or the credibility of the information tied to someone’s Twitter, Facebook, Pinterest, Vine, and Google+ accounts, but the United States government has made its decision. The United States government recently decided that a person’s social media presence could prove to be vital (to a number of different situations) and should be documented; this recent Politico article explores this development.

As the article explains, the United States government recently started requesting that foreign visitors provide their social media information upon arrival to the country. Since late December, visitors arriving on the visa waiver program have been prompted with a drop-down menu including various social media sites and space to enter their personal usernames. Although this is technically an optional request, many vehemently oppose the government’s decision to ask for this specific information.
While the US government has stood by its decision to ask and gather information related to visitors social media (in hopes of spotting potential connections to terrorist organizations like ISIS), many feel as if it is a violation of privacy. Even more so, people have lodged complaints about the lack of visibility into exactly how the US government is using this information. I feel as if this recent development would be virtually unopposed should the United States government solely be looking for and ideally identifying terrorist threats. However, as many (including my potentially jaded self) believe – there’s probably slightly more going on beneath the surface.
I have no doubt that access to visitors social media accounts could potentially produce leads and information about threats to our safety. My problem, and the problem that many Americans have mentioned, is that once that information is included on a form – it disappears into the bureaucratic secrecy that is our defense department (our whichever other department). In that sense, I think a little transparency wouldn’t hurt.
Failure of a Cultural Phenomenon: Vine
Students are all guilty of spending time online entertained by the sheer genius and stupidity of the Internet. Instead of studying for that CS or Physics midterm that will surely make us question our level of intelligence, we become distracted by the highly entertaining yet short videos and relatable memes sprinkled wide across social media platforms. Surely the founders of the Internet didn’t mean for us to waste precious time on such menial things, but these small bursts of laughter significantly impacted our mainstream media and entertainment. Ranging from the doge to the mannequin challenge, these cultural trends became a source of laughter and a method of bonding between our peers as people send or tag hilarious videos or pictures to friends.
Vine, a start up that was purchased by Twitter, quickly became a platform in which sprouts of creativity from amateur entertainers were created. Though first meant to be a video sharing tool that could co-exist with Twitter’s short text forms, its executives soon realized that more and more people were using it as a source of entertainment and outlet of ideas. It quickly became the number 1 downloaded app on iTunes just 6months after launch and gained over 200 million users. Its most popular users got millions of followers, money, and luxurious benefits from producing 6 second content. The lightening speed in which popular videos and pictures spread across social networks signifies a changed dynamic on how information and culture is translated between people. Interestingly, through informal rather than formal communication between people, the things we accept into social construct and norms are solidified.
Yet just a couple days ago Vine was deleted from the face of the Internet. Gone. Non-Existent. The large social media platform slowly dwindled into something that Twitter could not sustain. In addition to Twitter’s struggles to make a profit, Vine failed to sustain its popularity as its competitors began to add new features, such as Instagram and Facebook with assimilating videos into their platform. Others criticized the app for failing to take advantage of its initial success and monopolizing its place in the market.

Despite its initial success as an app that utilized the powerful tool of social networks, Vine ultimately failed to sustain itself. I wonder if this rapid success, but failure for longevity is just a characteristic of companies that base their success off the stability of their users through social networks. Though like a person is more incentivized to stay on a platform if others in their social network constantly uses it, the fierce competition for people’s short attention span makes it difficult for social media sites to succeed fully. Although this is just an assumption on my part, I really wonder how many social-media/network based companies are able to operate for more than a few years.
Link to article: http://www.theverge.com/2016/10/28/13456208/why-vine-died-twitter-shutdown
Ready or Not, there’s a New ‘Gatekeeper’ in Town … and you’re bound to ‘like’ him!
Spoiler alert: By the end of this article, you may come to the realization that you have just found yourself in a four-year maze where every escape passes through a host of ‘local gatekeepers’ that actively support Donald J. Trump. You know what that means? Each and every one of us will, directly or indirectly, support the 45th President of the United States of America, in the near future. If that doesn’t settle well for some, well, fear not, there is always an emergency escape if you need it from time to time (read on to find out).
Tomorrow marks the beginning of a ‘Trump White House’ for at least the next one thousand four hundred sixty days. However, I argue that we are in for much more than just a ‘Trump White House;’ we are entering a ‘Trump World.’ But let me soften the blow and make it an even playing field: we are leaving an ‘Obama Era.’ Therefore, the general framework in this post applies to all of our previous presidents because they each created the largest ‘affiliation network’ of their time – only difference is that their network was more subtle (both in sheer numbers and controversy) than the one Trump is creating given his past networks merging with the ‘presidential network’ that is inherited by every president.
The “TrumpWorld” article does a beautiful job setting up the dense network of Trump’s connections to individuals, organizations and industries. Every possible combination is present and growing as Trump’s minimal (relative to other entities) formal political affiliations expands to the max number of possible “friendships” as the leader of the free world. In other words, the U.S. President acts as a global gatekeeper between any two people or organizations since every citizen’s path passes through / relates to (not always in the literal sense) the president’s node to get to any other person or organization in the world. The star-like network graph below shows how Donald J. Trump is at the center of everything and then emphasizes some main “local gatekeepers” like Betsy DeVos of the education world, Jared Kushner of the real estate world and Wilbur Ross of the oldest, living generation and Wall Street. As you can see, here, the basic logic of networks creates a connection from you to Trump (just like you and Obama or you and Bush, etc.), satisfying the “six degrees of separation” concept, too. Okay, so we are all connected to one another, it’s a small-world phenomena, blah blah blah. That’s interesting but it’s not shocking. The fascinating part is how this larger than normal ‘affiliation network’ that Trump will be ‘staring in’ relates to the concept of homophily and triadic closure.
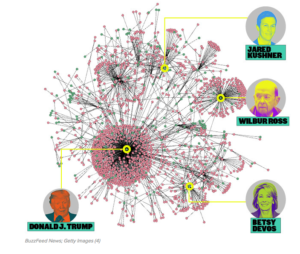
Homophily is the idea that we are naturally attracted to people that are similar to us for all types of relationships. Those similarities encapsulate all categories from race to age to personality traits. Given that Trump will be the global gatekeeper to the largest affiliation network to-date, we are all that much more connected which decreases the average distance between any two nodes (e.g. people, organizations, entities) and, then, lowers the lower bound of how low the “degrees of separation” can go as discussed in HW1. This creates the social belief that we are that much more similar (since we are that much more connected), increasing the likelihood that you will meet, affiliate, and, ultimately, like your friends’ friends. These likely connections in the near future satisfies the triadic closure concept that “two people who have a friend in common will likely become friends with each other at some point.” You tend to like your friends’ friends because of the built-in trust bond, potential for latent stress on relationship if you do not and similarity-liking concept explained earlier, which, ultimately, leads you to “liking” Trump from a network’s POV since you will, inevitably, be forming several close bonds with many of his active supporters and affiliates. Hey, it’s nothing personal – it’s just plain network effects.
I promised you an emergency escape. Unfortunately, no one can live in this escape but that is exactly what makes it a completely isolated network, untouched by everyone including Trump and all his affiliates so …
LIVE FROM NEW YORK, IT’S SATURDAY NIIIIGHHHHTTT! Enjoy.
Sources/Links:
https://www.buzzfeed.com/johntemplon/help-us-map-trumpworld?utm_term=.mqxkOKL3N#.feQqYEMbG
Just How Strong Are Weak Ties?
It is a commonly held belief that weak ties are more effective in helping you land a new job than strong ties. Our intuition might tell us that strong ties are more valuable because a close connection knows you better and naturally is more invested in your personal and professional success. But as Granovetter noted in his 1973 paper The Strength of Weak Ties, most people have significantly more weak ties than strong ones, and these weak ties may in turn allow them to tap into a much broader professional network. This leads to another question: does this conclusion about the strength of weak ties apply equally to everyone?
As researchers from Tufts University have discovered, both weak and strong ties play valuable roles in the job search process for people around the world, but the “value of a single strong tie is even more important for job seekers in countries with pronounced income equality.” For example, having just a single strong tie is more valuable in South Africa or Haiti as opposed to one formed in Sweden or the Netherlands, where there is greater socio-economic equality. Thus, job seekers should take their geographic location (or more specifically, the socio-economic balance of their location) into consideration when analyzing the strength of their professional networks.

Figure: People rely more heavily on strong ties in countries with greater economic disparity.
This research was novel regarding its use of a single data set (i.e., anonymous Facebook data from users’ social networks in 55 countries) in order to compare the strength of ties across international borders. Another surprising conclusion from the study was that more than 90% of Facebook friendships are considered weak ties, which is something to think about the next time you receive a friend request from someone you just met. For those readers who are surprised or even disillusioned by this looming 90%, consider how the presence of weak ties may actually add to your network by giving more value to those few strong ties you actually hold dear.
Zaza Pachulia: Potentially the Worst NBA All-Star Ever
The NBA released an article about Zaza Pachulia’s recent success in NBA all-star voting. Zaza Pachulia, the newly acquired center for the Golden State Warriors, is currently averaging 5.6 points per games, 5.8 rebounds per game and 0.5 blocks per game, with a modest player efficiency rating of 15.40 (the league average is 15). While Zaza fits the Warrior’s role nicely, his stats hardly compare to other Western Conference big men, such as Demarcus Cousins of the Sacramento Kings (averaging 28.0 points per game, 10.0 rebounds per game with a PER of 27.0) or Karl Anthony Towns of the Minnesota Timberwolves (21.9 ppg, 11.9 rbg, 22.8 PER). Why then, is Zaza Pachulia 2nd in the All-Star race, only behind his teammate (and former MVP) Kevin Durant for the Western Conference Frontcourt?
The answer is a new voting system by using social networks. To be selected to an All-Star team, the selection process is half determined by the fans’ vote (and 25% by the media, 25% by the players themselves). Ways for the fans to vote include using Twitter by including the player’s name and a hashtag, #NBAVote or using your Google Account to vote for your favorite players. While a quick search on Twitter can yield tweets with tens of thousands of retweets for certain players, the validity of selecting the best players is being questioned because of the bias of fans. The fans’ engagement with their team, size of the market of certain teams and use of social media can cause great bias in the selection of NBA All-Stars. For example, the tech savvy Bay Area, who’s team is having great success and who’s market is one of the biggest in the NBA currently has 6 players in the top 20 for Western Conference Voting. While potentially 4 are in legitimate conversation for all-star consideration, Zaza Pachulia and Andre Iguodala do not belong on the list.
Recently, Miami Heat center Hassan Whiteside publicly spoke against the legitimacy of the voting system. While he is putting up top of the league numbers (17.5 ppg, 14.3 rbg and a 22.08 PER), he is not even in the top 10 for Eastern Conference Frontcourt. Hassan was also angry about a player or a team’s ability to self-promote themselves to garner retweets and get votes. For example, Philadelphia 76ers center Joel Embiid posted this tweet (along with dozens of other tweets voting for himself). The self-promotion practice is legal by rules, but questionable in practice.
While Twitter Voting competition is bringing a lot of attention to the NBA, some of the biases are present in the polling results. Fortunately, the fan vote only accounts for half of the selection process, so outliers like Zaza Pachulia will probably not be an All-Star. But the practices of getting votes should be questioned in future all-star selection processes.
The Trees Speak
If you have ever walked over a grassy field or through a plot of forest, you will have certainly stepped over one of the most expansive, interwoven and complicated network structures that exist in biology. According to a recent Scientific American article “Dying Trees Can Send Food to Neighbors of Different Species”, the majority of the world’s plant life is connected by a “wood-wide web” of plants and fungi. Although this network of plants and fungi is believed to be nearly as old as much of the earth’s flora, it is only in the last century that florists and biologists have begun probing into the astounding effects of this interconnected structure.
The key-player that facilitates this connection between plants is the Rhizopogon fungus, which is only one of many mycorrhizal fungi. Like all classes of fungi, the Rhizopogon is able to scatter its roots far into its surroundings by producing a type of mushroom that is eaten by small mammals and which is then ‘reseeded’ into the ground through these animals’ excrement. Recent discoveries have indicated that once these fungi grow into the soil they bind to the roots of neighboring trees and plants. This process then commences the development of a network in which trees and plants can be observed as nodes, and the fungus linking them as the corresponding edges.
Given the multiplicity of fungi – particularly the Rhizopogon – the floral networks that have been established over millions of years are unimaginably vast. The following graphic shows the nodes and edges of such a network on a 30 by 30-meter plot of land, in which only two species of plants and fungi are observed.
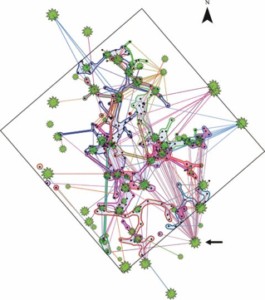
credit: https://blogs.scientificamerican.com/artful-amoeba/dying-trees-can-send-food-to-neighbors-of-different-species/
Even more remarkable than the complexity of this floral web, are the mutual benefits both plants and fungi derive from it. For one, by binding with plants, fungi can siphon off parts of the nutrients of their host vegetation, and in turn provide these plants with additional resources like water that their sprawling network of roots have collected. More surprisingly, however, trees can also choose to release additional resources into the roots of the fungi, in order to support surrounding vegetation in times of scarcity. This characteristic has most frequently been observed amongst dying and more mature trees, which will release a majority of their nutrients in one last “dying breath”, so as to support younger trees (particularly of their own species). Additionally, biologists have observed that by releasing toxins into the fungal network, trees can “give warnings” to the surrounding plant life of possible pathogens and insects in the area. Some scientists go so far as to posit that trees may even release certain signals to “threaten” plan life that is encroaching into their territory.
Although these mycorrhizal networks provide vital survival mechanisms for the world’s plant life, they are also threatened by increased climate change and logging. Scientists argue that in the past the ability for plants to reallocate resources may have provided important stabilizing effects against natural changes in the earth’s climate. Today, however, forests are declining at an unprecedented rate to dire consequences. These negative effects are compounded particularly for the fungal networks. In class, we have studied that if a key (local) bridge is removed between two nodes in a graph, the path between any two nodes may increase multifold (i.e. if the span of the removed edge is large). In biology, if we observe trees as nodes, logging a tree that forms a particularly important bridge may have disastrous effects on the efficacy of the nutrient allocation system enabled by this network. Mature trees, in particular, which provide the mycorrhizal web a majority of its nutrients are especially pivotal, but also more prone to being logged for their wood. Given the complexity of the mycorrhizal structure, it is difficult to measure the effect of logging any singular tree on the surrounding ecosystem. It is clear, however, that by clearing large paths of forest, humans may have begun splitting what once was a large subterranean network of fungi and roots into individual connected components. In the long run, doing so is likely to decrease the ability of forests to adapt to changing ecological conditions, and compound negative ramifications resulting from climate change.
While these discoveries paint a pessimistic picture of the future of our habitat, we should not underestimate the ability of the earth to evolve and repair itself. In so far as plant life goes, it seems to be biology’s natural equilibrium to return to a state of complex connectivity between organisms. We simply need to give our world the chance to do so.
Networks Led Us Astray: Election 2016
Millennials are now gathering their news from a multitude of sources beyond the 6 pm news show the Generation X was subject to. Stories are being shared on Facebook and Twitter, the previous day’s events are summarized and sent to inboxes and satirical stories and spoof news sources are indistinguishable from actual news. Through this proliferation, we are given increased freedom to choose the subset of news sources and stories we listen to. Given basic human tendencies, this subset begins to align more and more with our prior notions, cultures and views of the world.
We are able to ‘unfollow’ on Facebook and ‘mute’ of Twitter the people who share information or viewpoints that differ from our own and tune into the news stations that provide perspectives that match our interpretations of the world. Hence, we tend do construct networks composed of people who think and talk and post like us and provide a great sounding board for our own ideas, much like a homophily.
The article in The Ringer refers to network homophily and its impact on social media and polarizing perspectives. It provides an interesting insight on how it led some voters confused and flabbergasted by the results of the 2016 Election. People only tuned into sources who agreed with beliefs and those who’s political views contradicted with the people around them either chose to remain silent or tailored their networks to where they felt comfortable sharing their ideas.
Article Link: https://theringer.com/social-media-echo-chamber-2016-election-facebook-twitter-b433df38a4cb#.sqgrec4se
Navigating the Highway Network as a Self-Driving Car
As a future with self-driving cars draws near, it seems like more and more companies are trying to make their mark in this undefined space. Most recently, Amazon received a patent for their work on a highway network that manages the way self-driving cars navigate reversible lanes. The idea is detailed in a recent article published on Recode.net. Essentially, the idea describes a highway network that gives autonomous vehicles specific lane assignments on the roadway. The benefit is that the lanes are reversible; at different times of the day or to reduce congestion after a car accident, the direction of traffic flow for any lane can be switched.
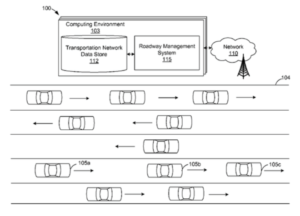
Figure: A drawing from Amazon’s patent detailing the differing lane assignments for the self-driving vehicles.
The current highway network, with on and off ramps and intersections as nodes and roadways as edges, serves the current way we drive quite effectively. However, self-driving cars provide an opportunity to rethink the current network, just as Amazon is doing. In the traditional highway network, edges are directed, in that traffic only flows one way on either side of a road. In Amazon’s new network, these directed edges can be flipped, simply by giving the self-driving cars a different lane assignment. In other directed networks, reversing a directed edge could be thought of as removing the edge and then adding the reversed edge. For example, on Twitter or Instagram, this would be like person A unfollowing person B at the same time person B follows person A. In Amazon’s highway network, the idea is similar: close the lane to southbound traffic and open it to northbound traffic, for example. If all cars on the roadway were self-driving, there would not need to be any signs or notifications to indicate the lane reversal, since the computers could simply assign cars to appropriate lanes.
Prior to reading this article, it seemed to me that designing a network was relatively straightforward: choose the nodes, choose the edges, and determine if the edges are directed or undirected. However, the article brings to light the idea that restructuring the way a network is designed could be incredibly valuable for meeting the goals of the network. What other ways could the highway network, or any network, be transformed in previously unthought of ways?
With this idealism, I thee wed…
According to government estimates, and found in this Washington Post Article, roughly 250 Americans have attempted to join ISIS Jihadists in Syria with one in six of those being women. So if my math skills don’t fail me, one in every six out of 250 total defectors is about 40 women. 40 women (since the article was written in 2015) chose to leave behind the freedoms we enjoy as Americans to join a terrorist organization in the middle east. How does this happen? By the way, that is just American women. Taking a look at Western-aligned women in total, those numbers at least double, warranting a look at how modern networks, including social networks and the basic understanding of human connections through various degrees of separation, create an ease of access between young women and evil people supposedly a world away.
I will quickly outline a few assumptions about this demographic to limit this discussion to the principle points. That is, some of these Western women are Muslim Americans, some are recent converts to Islam, and some have ties, whether family-based or from personal travel to the middle east. Aside from the probable existence of an affiliation network, whether built based on “push” from radical extremists targeting impressionable teens, or “pulled” from these Western citizens joining online groups, the sheer proximity of every one of us to a foreign terrorist is staggering.
This post will focus on another aspect of their defection – the root social necessities we seek as humans and the decisions we make when those connections are not present. This Huffington Post article says, “Some women launch their passage to ISIS driven by a youthful sense of adventure, secrecy, a romantic rebellion against the establishment. Others become indoctrinated by the war Islam wages against “American/European corruption.” ISIS recruiters allure young women by marriages and marital bliss.” In some cases these women seek out a sisterhood aligned with their religious beliefs. In other, more disturbing instances, ISIS recruiters manipulate these women with promises of luxury. Making the decision to join ISIS is one step. Why is it that these women can then so easily locate and build relationships with these people?
Not belonging to a social network with many, if any, strong ties (outside of family) may lead these women to ditch their lives of liberty and freedom for false promises of happiness in a perceived utopian society. One could further posit the desire for the emotionally neglected to throw a weak tie out into the world like a grappling hook to see what kind of attention, belonging, and acceptance they can latch on to. The only problem is that ISIS is waiting on the other end to grab hold and recruit these women. Social media is the platform for which the universal, physical handshake of an acquaintance has been replaced with a digital handshake created between two separate worlds, miles apart. A naïve curiosity can quickly morph into a new idealism, especially at the hands of skilled manipulators.
Access to ISIS propaganda is the key to recruiting. In the giant component included in the global map of social media connections, the technology available to update a photo stream for my family to see is also the technology that puts me less than six clicks away from an Islamic Extremist (or so one would theorize based on a more modernized view of “six degrees of separation”). In fact, Facebook proved that the average degrees of separations between users are now roughly four.
The access that exists today – the access that ISIS has to the world’s population through digital propaganda, and the access that American youth have to receive and digest that propaganda, is clearly one of the most dangerous realizations of social networking in modern society. And these evil players not only have access to communication with these impressionable Americans, they have access to all of the personal data needed to influence and manipulate their decisions. No longer can an anonymous chain letter connect the world – our profile pictures tied to our family data, hobbies, interests, and career info creates a path from an American teenager in Alabama to a Terrorist in Syria.
This isn’t a new security threat in the eyes of the government, but it might be a new threat in the eyes of the public. Our world is becoming more digital every day and there needs to be some awareness of the danger that exists from the connectivity that social media and online social networks created.
Forget about trying to connect yourself to Kevin Bacon, you should be concerned with how close your daughter is to receiving a friend request from Abu Mohannad al-Sweidawi.
Welcome
Welcome to the course blog for MS&E 135 Networks at Stanford University. This course explores how diverse social, economic, and technological systems are built up from connections, and how the study of networks can help us understand these systems.
Enrolled undergraduate students will be writing regular posts on varied subject matters and current events related to the course. Topics include: networked markets, social networks, information networks, the aggregate behavior of crowds, information diffusion, the implications of popular concepts such as “six degrees of separation” and the “friendship paradox.”
The blog is visible to the public, however only students and course staff are able to post and comment. Students should refer to the course blog guide for more information.
